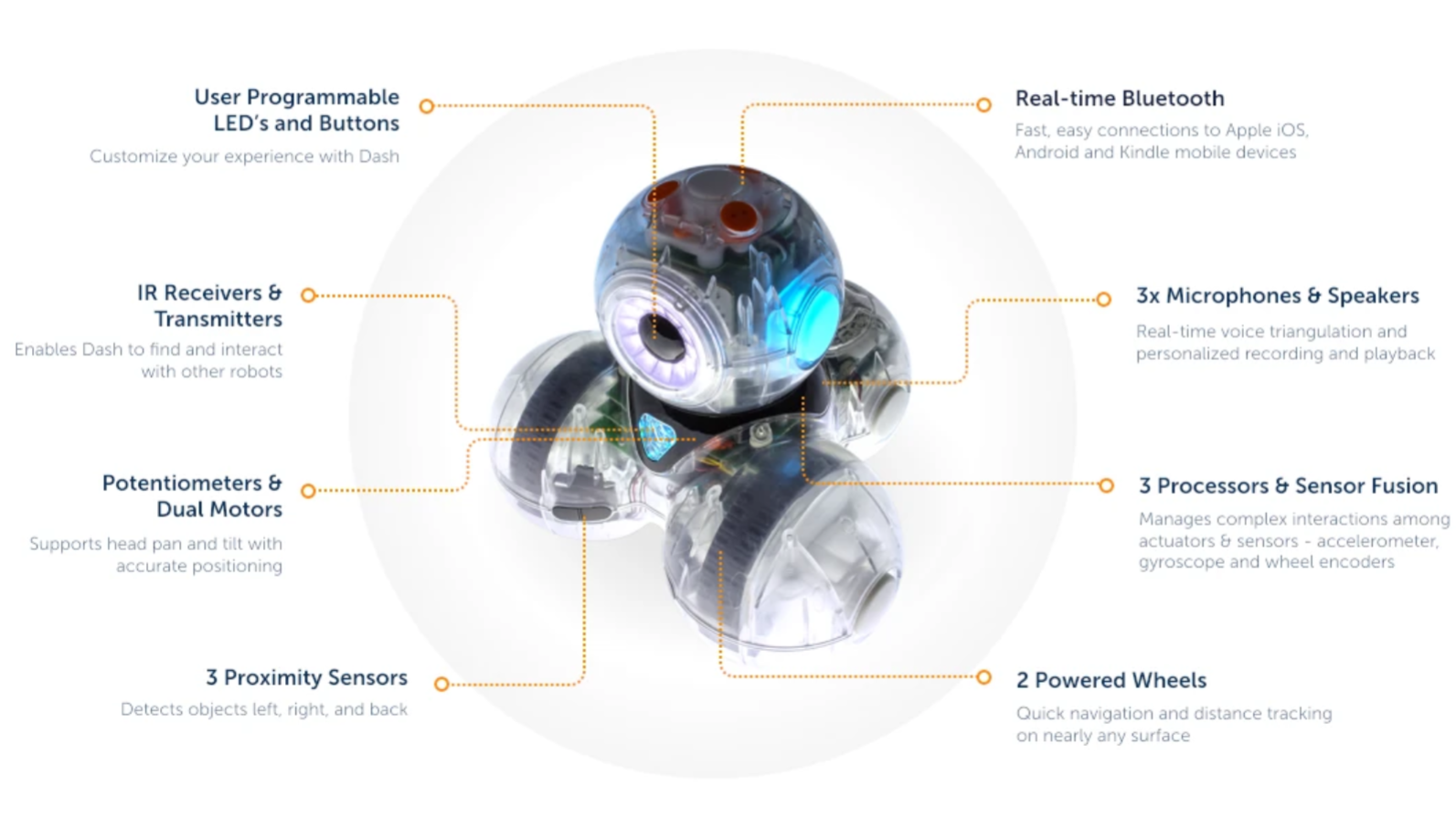
One of the joys of browsing secondhand shops is the possibility of finding old, perhaps restorable or hackable, electronics at low prices. Admittedly, they usually seem to be old flat-screen TVs, cheap speakers, and Blu-ray players, but sometimes you find something like the Dash, an educational toy robot. When [Jonathan] came across one of these, he decided to use it as a turtle robot. However, he found the available Python libraries insufficient, and improving on them required some reverse-engineering.
While [Jonathan] was rather impressed with the robot as it was – it had a good set of features, and thought had clearly been put into the design – he wanted a more open way to control it. There was already a quite useful, official Python program to control the robot over a BLE connection, but it only worked with Python 2 on OS X ([Jonathan] theorizes that it might have been written as a development tool, open-sourced, and not diligently supported afterwards). There were also a few third-party libraries ported to Python 3, but they all seemed to be missing some important features.
All the newer libraries were limited because the official library passed commands to an OS X binary, which handled the actual communication, so anyone wanting to do everything in Python would have to reverse-engineer the communications protocol. [Jonathan] therefore used Ghidra to decompile the binary. He first found the JSON structure used for message data, followed by a function that reads command information and sets up packets, and a mapping between Python command names and command IDs. Once he found the section that creates packets from data, he was able to port the program to Python 3. Interestingly, examining the binary revealed some previously unknown commands that appear to be capable of defining autonomous behavior.
We’ve previously seen Ghidra used on devices ranging from a camera to a router; if you’d like to learn more, there’s a HackadayU course on it.
This articles is written by : Fady Askharoun Samy Askharoun
All Rights Reserved to Amznusa www.amznusa.com
Why Amznusa?
AMZNUSA is a dynamic website that focuses on three primary categories: Technology, e-commerce and cryptocurrency news. It provides users with the latest updates and insights into online retail trends and the rapidly evolving world of digital currencies, helping visitors stay informed about both markets.